See how Apporto compares to today’s most popular virtual desktop providers.
Learn how Apporto helps enable a more secure mobile workforce with its Zero Trust Virtual Desktops.
See how Apporto compares to today’s most popular virtual desktop providers.
Learn how Apporto helps enable a more secure mobile workforce with its Zero Trust Virtual Desktops.
Although all these solutions make efforts to address the growing security concerns, they fall short of zero trust.
While VPN technology can provide online privacy through a private network accessed from a public internet access point, it fails to offer the security that today’s companies need. VPNs do not secure the most vulnerable part of a network - the end point.


The central location of a VDI solution can remove some security vulnerabilities. However, with the rise of bring-your-own-device to the remote working , these legacy-based systems cannot easily maintain the governance and security required. Significant resources are required to build and maintain new security protections on a VDI system.


The movement of operating systems, applications, and data to the cloud through third-party virtual desktop DaaS solution providers also attempts to address security concerns. While many DaaS vendors prioritize redundancy, backup and recovery protocols, and added security services for customers, they fall short of zero trust.

The next-generation virtual desktop that helps you achieve zero trust.


Unlike alternative approaches, all communications between the end user and the servers use HTML, therefore there’s no need to worry about the security posture of the endpoint device.
Apporto uses advanced autoscaling and optimization algorithms to keep costs low. Customers pay a predictable low cost. Everything is already included; that means no systems integrators, no implementation and no consulting fees.
Built from the ground up as a SaaS solution, Apporto takes care of all the infrastructure so organizations can focus on what matters to them. Customers report significant savings in IT time, which enables them to focus on other tasks. Apporto handles backup, recovery, monitoring, antivirus, and more as part of its service. All the time-consuming tedious tasks are managed so companies can focus on what matters.
Users can perform all their critical tasks, including sound video and conferencing, in the virtual environment. This ensures that all traffic goes through the corporate security stack.
Threat actors are increasingly using active web content to deliver the most sophisticated types of ransomware. Apporto transforms active web content into harmless pixels and text.
Users are automatically provided access to only the apps, data and network resources they need based on group affiliation.This prevents unauthorized access and lateral movement.
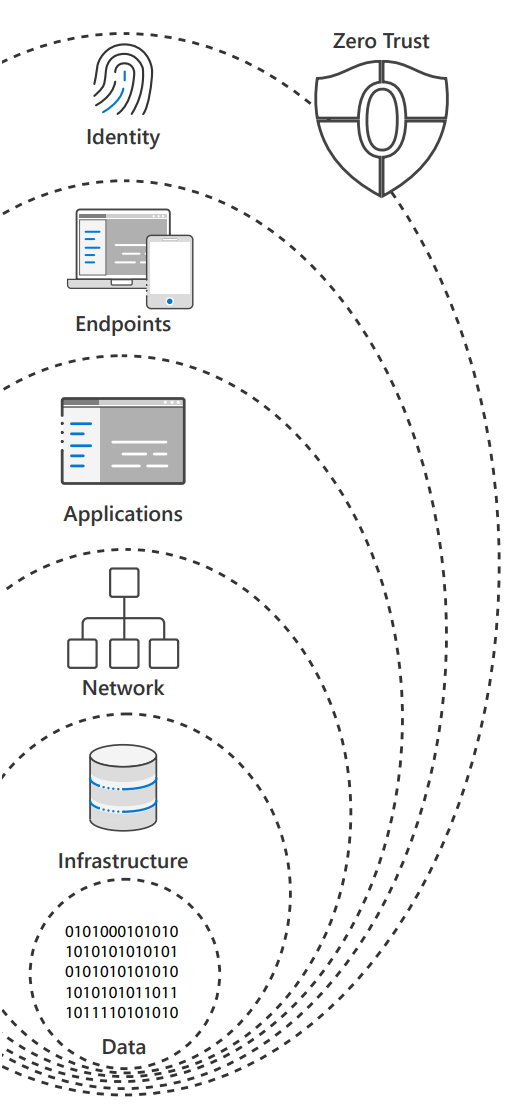
Zero Trust starts with identity, verifying that only the people, devices and processes that have been granted access to your resources can access them.
Next comes assessing the security compliance of device endpoints - the hardware accessing your data - including the IoT systems on the edge.
This oversight applies to your applications too, whether local or in the Cloud, as the software-level entry points to your information.
Next, there are protections at the network layer for access to resources – especially those within your corporate perimeter.
Followed by the infrastructure hosting your data on-premises and in the cloud. This can be physical or virtual, including containers and micro-services and the underlying operating systems and firmware.
And finally, protection of the data itself across your files and content, as well as structured and unstructured data wherever it resides