Stop Using RDP for Remote Access
In today’s ever-changing hybrid and remote working environments, it’s often necessary for users to connect back to their company-issued desktop PC sitting on their desk. This might be due to a custom security configuration, specialized software, or restricted access to sensitive data. Regardless of the need, a popular way of establishing this connection is through a remote desktop connection utilizing the Microsoft standard protocol of Remote Desktop Protocol or RDP.
But a recent joint warning from the FBI, along with the US Cybersecurity and Infrastructure Security Agency (CISA) and the Australian Cyber Security Centre (ACSC) indicate that attacks against this popular connection method are on the rise, getting more sophisticated, and seeing some breaks in the connection encryption.
Source: https://www.theregister.com/2023/05/17/fbi_cisa_bianlian_advisory/
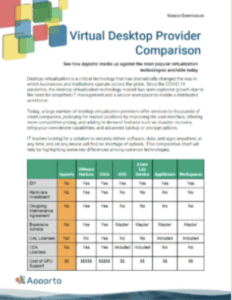
So what other options exist? Luckily, there is a large list of options available from different vendors, but which is best and more importantly, which provides the best security and performance for users? Here is a comparison chart of some of a few of the most popular options:
Feature | Apporto | VMware Horizon | Citrix | Splashtop | TeamViewer |
Remote Desktop Access | Yes | Yes | Yes | Yes | Yes |
Cross-Platform Support | Yes | Yes | Yes | Yes | Yes |
Client Required/ Recommended | No | Yes | Yes | No | Yes |
Agent Deployment Required | No | Yes | Yes | Yes | Yes |
File Transfer | Yes | Yes | Yes | Yes | Yes |
Remote Printing | Yes | Yes | Yes | Yes | Yes |
Multi-Monitor Support | Yes | No | Yes | Yes | Yes |
Collaborative Features | Yes | No | No | No | Yes |
Two-Factor Authentication | Yes | Yes | Yes | Yes | Yes |
DIY Deployment? | No | Yes | Yes | Yes | Yes |
TCO | Low | High | High | Medium | Medium |
One of the challenges with all remote desktop solutions is maintaining high levels of security without compromising user experience. These are some of the common security concerns when providing users with remote access to desktops:
Authentication and Access Control: Ensuring proper authentication mechanisms and access control is crucial to prevent unauthorized access to remote desktops. Weak passwords or inadequate authentication protocols can pose security risks.
Data Encryption: Remote desktop solutions should employ strong encryption methods to protect data transmitted between the local and remote systems. Without proper encryption, sensitive information can be intercepted and compromised.
Endpoint Security: The security of the local device accessing the remote desktop is vital. If the local device is infected with malware or compromised, it can potentially compromise the security of the remote desktop environment as well.
Network Security: Remote desktop connections often rely on network infrastructure that may be susceptible to security breaches. Employing secure network protocols and implementing appropriate network security measures, such as firewalls and VPNs, is crucial to protect against unauthorized access or data interception.
Auditing and Monitoring: It is important to have mechanisms in place to monitor and log remote access sessions. This helps in detecting any suspicious activity, identifying potential security breaches, and ensuring compliance with security policies.
Third-Party Security: When using remote desktop solutions, it’s essential to consider the security practices and track record of the solution providers. Ensure that they follow industry best practices, regularly release security updates, and have a robust vulnerability management process.
Session Hijacking: Remote desktop sessions can be vulnerable to session hijacking attacks, where an attacker takes control of an active session. Implementing techniques like session encryption, session timeouts, and regularly rotating session IDs can mitigate the risk of session hijacking.
Data Leakage: Remote desktop solutions may allow file transfer between local and remote systems. Ensuring proper controls and policies are in place to prevent unauthorized or accidental data leakage is important to protect sensitive information.
Virtual Desktop Provider Comparison
Remote Connections with Apporto
Apporto is a fully managed cloud desktop platform with a 100% ‘Would Recommend’ rating by Gartner-verified peer reviews. The inclusion of remote PC connections makes this choice the best on the market for securing remote access to internal systems.
At Apporto, security and user experience are at the core of our solution. First, all connections are made using a modern browser secured with HTTPS encryption. This solves the concern of endpoint security and the need for companies to issue and manage expensive devices to their users. In addition, the browser creates a very strong security boundary between the user’s endpoint and internal company resources. This is completed without the need for a VPN client which can be tricky to configure, can require ongoing updates and support, and sadly, is now a very common attack vector by bad actors.
Further, the Apporto solution provides numerous layers of protection including cloud desktop protection, intrusion detection, web application firewalls, deep packet inspection, and ongoing backups of both infrastructure and user data where present. All deployments follow standard cloud best practices for zero-trust security and least privilege access to resources and are monitored by security engineers 24x7x365.
Finally, Apporto’s connection to internal desktop PCs is via a direct connection using existing security controls and offering users near-native performance from any device. This truly is the best approach to maintaining security and user experience.
Learn more: https://www.apporto.com/remote-hybrid-work
Happy Computing!